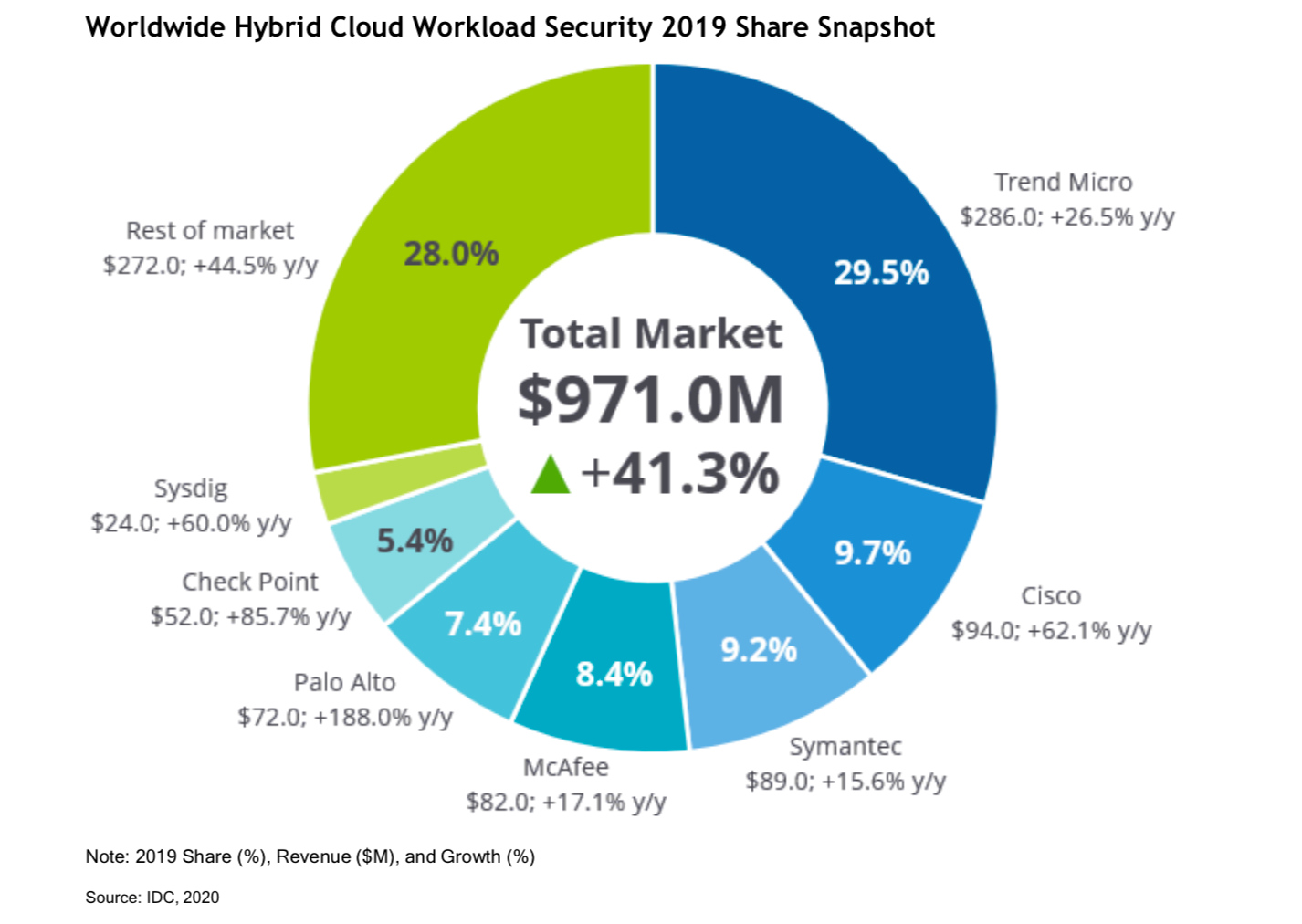
Trend Micro has been ranked #1 in IDC’s report,
“Worldwide Hybrid Cloud Workload Security Market Shares, 2019: Vendor Growth Comes in All Shapes and Sizes.” (June 2020)
At 29.5% market share, Trend Micro has three times that of the number two vendor.
IDC believes that Trend Micro has continued to invest in its hybrid cloud workload portfolio capabilities with the launch of the Trend Micro Cloud One™, which has enhanced our cloud security posture management offering, application security, and more.
This is in addition to the support Trend Micro offers for virtual, public cloud, and container environments, with seamless integration across Amazon Web Services (AWS), Microsoft® Azure™, and Google Cloud Platform™. In the report’s executive summary, the independent research firm states that, “Trend Micro is the dominant leader in SDC workload protection.”
With the arrival of Trend Micro™ XDR and Trend Micro Cloud One, we are uniquely positioned to continue to increase our market share and remain innovators in our field. In our view, IDC’s Worldwide Hybrid Cloud Workload Security Market Shares report places Trend Micro as the definitive leader in cloud workload security.
Trend Micro respects your privacy. Read our privacy policy.
Thank you! You will receive an email shortly with a link to the research report.
1.) “Architect for consistent visibility and control of all workloads, regardless of location, size, or architecture,” as per Gartner’s report.
We believe Trend Micro Cloud One™ (SaaS) and Trend Micro™ Deep Security™ software provides comprehensive visibility and control of workloads across physical and virtual data centers, as well as public and private cloud environments within Microsoft® Windows®, Linux®, traditional workloads, containers, and serverless. Both solutions provide visibility and detection of workloads scaling up and down through cloud provider (AWS, Microsoft® Azure™, Google Cloud Platform™ and VMware®) connectors.
Section 1 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 1 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 1 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
2.) “Require cloud workload protection platform (CWPP) vendors to support containers with planned solutions for serverless. Be open to point solutions if your legacy vendor doesn’t meet your container requirements,” as per Gartner’s report.
We believe Trend Micro Cloud One™ – Workload Security and Deep Security software provides containers with runtime detection and protection for the container’s platform, traffic, and applications. Trend Micro also supports serverless environments with detection and protection from Trend Micro Cloud One™ – Application Security.
Section 2 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 2 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 2 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
3.) “Extend workload scanning and compliance efforts into development (DevSecOps), especially with container-based and serverless function platform as a service (PaaS)-based development and deployment,” as per Gartner’s report.
Trend Micro Cloud One™ – Container Security and Trend Micro™ Deep Security™ Smart Check software extends container-based scanning to the development environment. Application Security allows development teams to seamlessly integrate security libraries for detection and protection of serverless function, PaaS-based development and deployment. Trend Micro Cloud One™ – File Storage Security also extends anti-malware capabilities to cloud file and object storage services that are often used with cloud-based application development. We believe this allows us to meet the recommendation above.
Section 3 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 3 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 3 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
4.) “Require CWPP offerings to expose all functionality via APIs,” according to Gartner.
Trend Micro takes an API-first approach with both Trend Micro Cloud One (SaaS) and Deep Security software, which we believe allows us meets the recommendation above. Using APIs, we ensure that customers can automate and implement DevSecOps’ practices in their organization like deployment, health checking, policy updates, reporting, and etc.
Section 4 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 4 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 4 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
5.) “At runtime, replace antivirus-centric strategies with a “zero-trust execution”/default deny approach to workload protection where possible, even if used only in detection mode,” as per Gartner’s report.
Workload Security provides anti-malware, with behavioral analysis and machine learning, as well as application control that uses a default-deny approach for detection or protection of workloads. We believe this allows us to meet the recommendation above.
Section 5 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 5 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 5 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
6.) “Architect for CWPP scenarios where runtime agents cannot be used or no longer make sense,” as per Gartner’s report.
For scenarios where runtime agents cannot be used or no longer make sense, Trend Micro offers anti-malware, vulnerability, and secret scanning in the development pipeline. With Container Security and Application Security, development teams can integrate security libraries for detection and protection in PaaS-based environments. We believe this allows us to meet the recommendation above.
Section 6 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 6 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 6 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
7.) As per Gartner’s report, “Require CWPP vendors to offer integrated cloud security posture management (CSPM) capabilities to identify risky configurations.”
Trend Micro offers integrated cloud security posture management (CSPM) with Trend Micro Cloud One™ – Conformity, real-time continuous assurance and visibility over your cloud infrastructure. We believe this allows us to meet the recommendation above.
Section 7 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 7 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 7 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Simplify your decision
ShowHide Section - Column 1. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
ShowHide Section - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
ShowHide Section - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
ShowHide Section - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.