Trend Micro has been ranked #1 in IDC’s report, “Worldwide Cloud Security (Software-Defined Compute Workload Security and Firewall Fabric) Market Shares, 2018: Protecting Workloads in Hybrid and Multicloud”.
At 35.5% market share, Trend Micro has almost triple the market share of our closest competitor.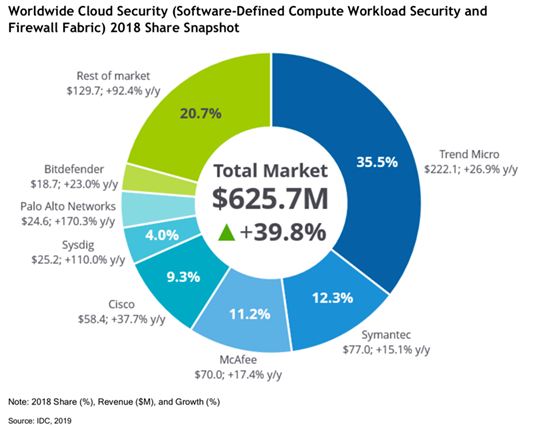
IDC believes that Trend Micro has steadily built out its hybrid cloud workload portfolio capabilities for virtual, public cloud, and container environments, offering tight integration with AWS®, Microsoft® Azure™, and Google Cloud Platform™. In the report, the independent research firm concludes, “Although the future is not written, Trend Micro is the dominant player in the market”.
In our view, IDC’s Worldwide Cloud Security Market Shares places Trend Micro as the definitive leader in cloud workload security. With the arrival of Trend Micro™ XDR and Trend Micro Cloud One™, we are uniquely positioned to increase our market share and remain innovators in our field.
But don't just take our word for it, read a free copy of the report, compliments of Trend Micro.
Trend Micro XDR
Multi-layered detection and response in a single platform
Do you share our vision for taking a broader perspective on detection and response? What would it mean to you if you could:
| Benefit from powerful artificial intelligence (AI) and expert security analytics to correlate data from your environment and Trend Micro’s global threat intelligence. Produce fewer, higher fidelity alerts for better, earlier detection. |
| Connect email, endpoint, server, cloud workloads, and network to give a wider view and better context to identify threats more easily, and contain them more effectively. |
| Use one console with one source of prioritized, optimized alerts supported with guided investigation. Simplify the steps to achieving a full understanding of the attack path and the impact on your organization. |
Watch “XXXXXXXXXXX” for a look into one of the most common security issues Trend Micro XDR helps solve.
(Infographic info)
<CTA: Learn more>
Read ESG’s exclusive white paper, XXXXXXXXXXX, and get valuable insight into:
- The evolution of threat detection and response and where it will bring us in the future
- The value of detection and response beyond just endpoint
- The growing value as you connect more security layers
<CTA: Read white paper>
Section 1 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 1 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Trend Micro XDR for Users
Start with XDR today by doing more with EDR
You get automated detection and response, along with root cause analysis and impact assessment, and indicators of compromise (IoC) sweeping and hunaing across endpoints, servers, and email. Connect these security layers and benefit from:
| Wider visibility and more insightful investigations across vectors—including email, which is is the #1 attack source |
| Easier-to-identify-and-action responses |
| The ability to reduce the spread and impact of threats |
Exclusive Webinar – XXXXXXXXXXXX
Wednesday, August 28th
X p.m. ET
XX min
Hosted by XXXXXXXXXXXXXX
<CTA: Register now>
Read our XDR Solution Brief for insight into:
XXXXXXXXXXXXXXXXXXXXXXXXXX
<CTA: Read solution brief>
View our XDR demo video and learn:
XXXXXXXXXXXXXXXXXXXXXXXXXXXX
<Video image>Ex
Section 2 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 2 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Trend Micro Managed XDR
Alleviate resource and skills constraints
Our Managed XDR Service augments your team with Trend Micro’s passionate threat experts, to provide you with:
| 24/7 critical alerting and monitoring |
| Incident prioritization and investigation |
| Root cause and impact analysis |
| Recommendations on remediation and preventative measures |
| Incident reporting and executive reporting on security posture |
Cybersecurity Research Reveals the Good, Bad and Ugly of TwitterAugust 7 at 10:30am | and12:00pm | August 8 at 10:30am | and 12:00pm | Erin Johnson, Trend Micro Research Communications  Trend Micro Research used available Twitter data to find how the platform is being used across the security landscape – for good, bad and ugly reasons. Are you a security engineer who is curious how Twitter can inform your threat intelligence and strategy? Or maybe you’re wondering how criminals are leveraging social platforms to enable attacks and attract victims? Come hear what we found – it might surprise you |
Section 3 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 3 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 4
Section 4 - Column 1. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 4 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 4 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 4 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 5
Section 5 - Column 1. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 5 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 5 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 5 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 6
Section 6 - Column 1. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 6 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 6 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 6 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 7
Section 7 - Column 1. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 7 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 7 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 7 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
