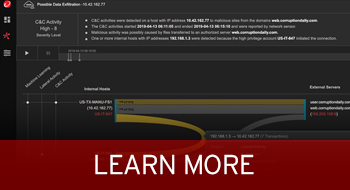
EDR is simply not enough
Threat actors don’t start and stop at the endpoint. When you are looking at just one layer, you only see a fragment of the malicious activity. You can’t detect multiple isolated activities as being part of the same incident. As part of our unified cybersecurity platform, Trend Micro Vision One is purpose-built to deliver deep data and correlated detection analytics across security layers so IT teams can see the full picture.
Backed by essential intelligence
Trend Micro’s solution and analytical expertise is paired with Trend Micro Research, our global threat investigation organization that powers our solutions, giving you the tools you need to enable organizations to mitigate cyber risk. Intelligence is never charged as an add-on; it is built-in and foundational to every solution we offer.
Section 1 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Too little, too late?
Ransomware, phishing, and fileless threats have become more sophisticated and advanced, and attacks are now measured in seconds, not hours or days. Trend Micro Vision One delivers key prevention and fast detection techniques that legacy EDR vendors like CrowdStrike can’t. Solutions that promote comprehensive prevention as a proactive measure, alongside detection and response, are essential.
Extended detection and response purpose-built from the ground up
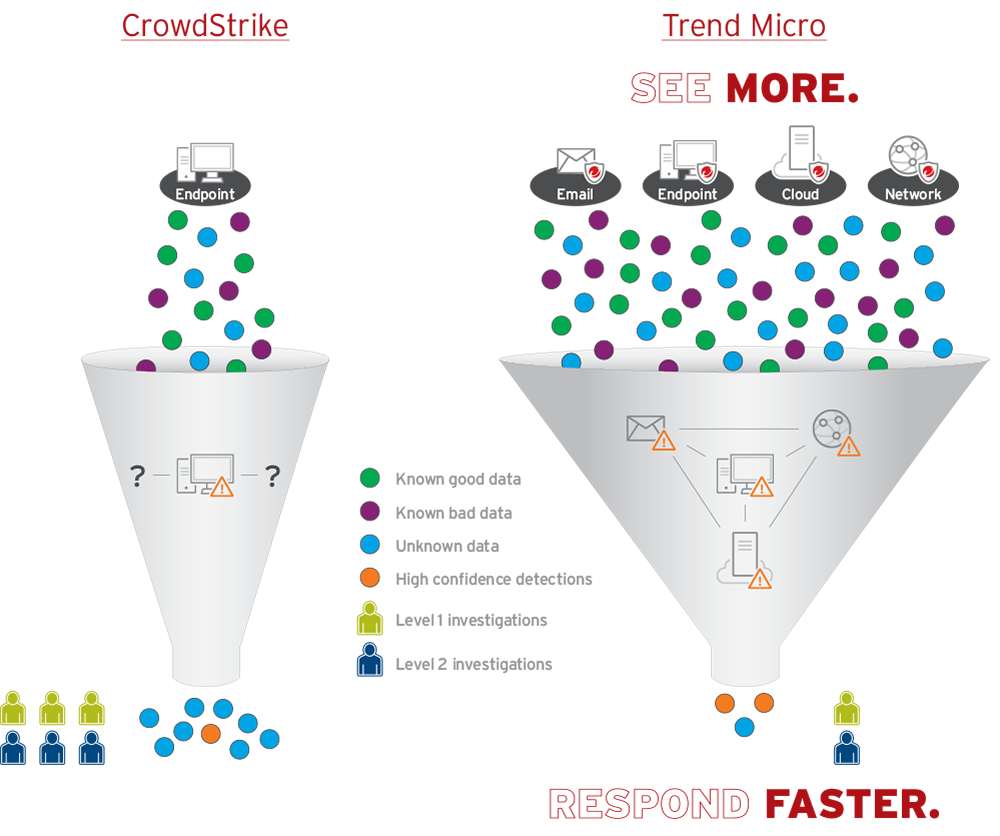
Legacy EDR vendors like CrowdStrike have attempted to add additional capabilities to their existing endpoint detection solutions and have only expanded their scope by relying on third-party products. Loose integration and info sharing with third parties is not true XDR. Trend Micro Vision One gives security teams industry-leading solutions, powered by our native security stack, for full unified detection and response capabilities.
Extended detection and response purpose-built from the ground up
First-generation EDR vendors like CrowdStrike have attempted to add additional capabilities to their existing endpoint detection solutions and have only expand their scope by relying on third-party products. Loose integration and info sharing with third-parties is not true XDR. Trend Micro XDR gives security teams industry-leading solutions, powered by our native security stack, for a fully unified detection and response capability.
Section 2 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Where Trend Micro solutions stand out
FASTER THREAT DETECTIONA blend of prevention and detection techniques to identify and block threats immediately, minimizing or eliminating damage and data loss. |
|
|
Machine Learning |
We leverage machine learning for pre-execution and runtime analysis with specific models for different types of files so you can be assured that, even before you click, we’ve checked all files to ensure that it exhibits no malicious intent. This provides your business with a huge benefit by providing detection accuracy and lower false-positive rates. Is your vendor only using machine learning on executable files? If so, they’re not acting fast enough, leaving you vulnerable. |
|
Signatures |
We use polymorphic signatures to quickly cut out the noise by blocking known-bad files—a highly effective and proven way of blocking known malicious files in rapid time. Check that your vendor isn’t using inefficient file hashes to avoid re-scanning known-bad files. Trend Micro can detect variations that occur within malware families without requiring signature updates. |
|
Behavior-Based Protection and Detection |
We use a mix of both runtime machine learning and expert rules to detect malicious behavior, blocking threats in milliseconds. Our behavioral engine makes its decision locally and lightning-fast. Does your vendor possess rapid detection efficacy? |
|
Virtual Patching / IT Hygiene |
Trend Micro offers virtual patching to protect earlier and more effectively, blocking exploits on arrival—especially with critical servers and workloads where it is difficult to apply vendor patches. In addition, our virtual patching is very timely, powered by passionate vulnerability research teams, including our Trend Micro™ Zero Day Initiative™ (ZDI). Are you partnering with a vendor lacking proper virtual patching (host based IPS)? This means you’re relying on outdated runtime behavioral techniques to block exploits. |
STRONGER FOR SERVER WORKLOADSThreats target servers differently. A different blend of defenses is required. |
|
|
Workload Discovery and Auto Scaling |
Workloads are vulnerable from the moment they are instantiated. Trend Micro provides built-in workload discovery capabilities, integrating with Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform™, VMware, and Microsoft Active Directory. Does your security get configured and deployed automatically when new workloads are instantiated? Trend Micro assures this will happen, even as a part of the build process or through your favorite deployment tools. |
|
Protecting Linux |
With Linux now representing nearly half of the worldwide server deployments, this growth has resulted in the increase of severe malware attacks that specifically target Linux servers. Inquire if your vendor offers strong coverage for all versions of the Linux operating systems. Trend Micro Cloud One™ – Workload Security modular feature set is highly similar across Microsoft Windows and Linux. |
|
Protection for current and legacy workloads |
A substantial portion of cloud workloads is based on Linux. Trend Micro’s platform support extends across current and legacy operating systems (Windows and Linux), including extensive Linux builds and hundreds of Linux kernels, Solaris™, AIX, and HP-UX Ask your vendor if their platform support is broad enough to protect legacy workloads. |
BROADER DETECTION AND RESPONSE BEYOND ENDPOINTSTrend Micro Vision One gives customers’ SOC/IR teams visibility across email, endpoints, servers, and networks, so they can detect and respond to threats more quickly and effectively. |
|
|
Search and Threat Hunting Platform |
Trend Micro provides a full range of indicators of compromise (IoC) sweeping capabilities, including the ability to sweep across email, endpoint, and network servers, giving you full visibility across your estate. Is your vendor only focusing on the endpoint? If so, you may be missing attacks targeting servers, email, and unmanaged devices. |
|
Investigating across your organization |
Trend Micro enables SOC/IR teams to hunt for threats that may have evaded detection, as well as investigate threats that were successfully blocked. Can you vendor investigate email and network data? If not, they’re slowing down the scope and speed of hunting increased tenfold across your organization. |
|
Extending your Security Team |
Trend Micro™ Managed XDR analysts are skilled at interpreting data from our industry-leading solutions. Analysts provide a step-by-step response action plan to remediate and help recover from the threat. Managed XDR frees up security analyst teams so they can spend more time on the most sophisticated attacks, in addition to maturing strategies and processes. Unlike CrowdStrike Overwatch™, Managed XDR is not just limited to endpoints but also covers email, servers, cloud workloads, and networks. |
A Leader in 4 Key XDR Building Blocks
Named a Leader, The Forrester Wave™: Endpoint Detection and Response (EDR), Q2 2022
“Organizations that want a platform to deliver cross-telemetry integration of traditional security tools and top customer service will benefit from a relationship with Trend Micro.”
Named a Leader in The Forrester New Wave™: Endpoint Detection and Response (XDR) Providers, Q4 2021
“Trend Micro is the best fit for companies that need a robust, easy to operate security suite.”
Named a Leader in The Forrester Wave™: Endpoint Security-as-a-Service, Q2 2021
“Its extended detection capabilities are robust and accessible from Trend Micro Vision One™...”
Named a Leader, The Forrester Wave™ Enterprise Email Security, Q2 2021
“Email security is part of Trend Micro’s aggressive (Trend Micro) Vision One™ XDR strategy which combines endpoint, network, and email for threat detection and response.”
Faster, Stronger, Broader

- Faster threat detection: Trend Micro has a blend of prevention and detection techniques to detect and block threats immediately, minimizing or eliminating damage and data loss.
- Stronger for server workloads: Threats target servers differently. Therefore, servers require a different blend of defenses.
- Broader detection and response beyond endpoints: With Trend Micro Vision One, customers’ SOC/IR teams get visibility across endpoints, email, servers, and networks, and as a direct result, can detect and respond to threats more quickly and effectively.
- Broader detection and response beyond endpoints: With Trend Micro XDR, customers’ SOC/IR teams get visibility across endpoints, servers, email, and networks, and can detect and respond to threats more quickly and effectively.
Section 5 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
See what you’ve been missing
Section 7 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.