
External Attack Surface Report
Discover exposure risks hiding in your internet-facing assets
Trend Micro is recognized as a Representative Vendor in the 2024 Gartner® Market Guide for Network Detection and Response (NDR) report.
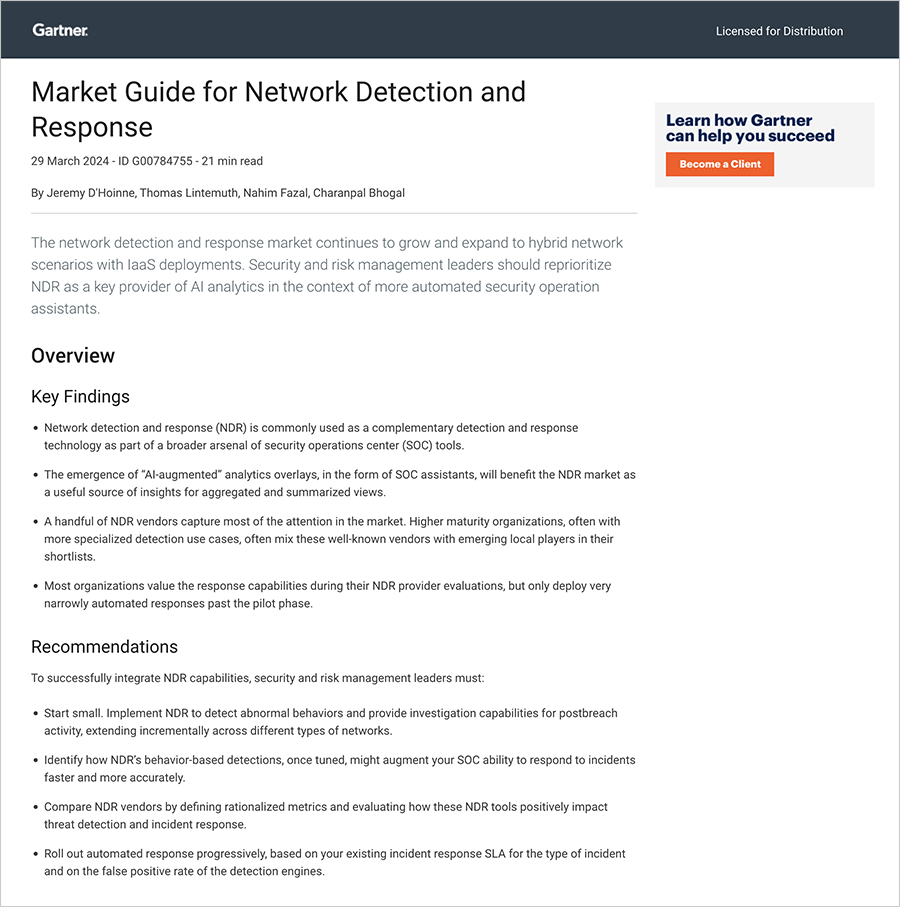
You can use a Market Guide to understand how the status of an emerging market aligns with your future plans. In addition, since Gartner has published over 100 Market Guide research notes, IT and strategic leaders can gain a broad view of many markets, including mature and smaller markets, in an easy-to-read format.
According to Gartner, the network detection and response market continues to grow and expand to hybrid network scenarios with IaaS deployments. Security and risk management leaders should reprioritize NDR as a key provider of AI analytics in the context of more automated security operation assistants. 1
1. Gartner Market Guide for Network Detection and Response, Jeremy D'Hoinne, Thomas Lintemuth, Nahim Fazal, Charanpal Bhogal, 29 March 2024
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used here in with permission. All rights reserved.

Agenda Table Headline
| Agenda Day | Session | Speaker |
|---|---|---|
| 8:00 - 8:30 | Reception Coffee | |
| 8:30 - 9:00 | Welcome & Opening Words | Mark Hamill - Manager Cyber Threat Intelligence |
| 09:30 - 10:00 | Keynote 1 | Carrie Fisher - Director Product Manager & Operations |
| 10:00 - 10:30 | Lunch Break | |
| 10:30 - 11:00 | KeyNote 2 | Anthony Daniels - Product Manager |
| 11:00 - 11:15 | Coffe Break |
Overlapping Image Section Headline

Lorem Ipsum is simply dummy text of the.
Lorem ibsumLorem Ipsum is simply dummy text of the printing and typesetting industry?
Lorem ibsumSimplify your decision
ShowHide Section - Column 1. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
ShowHide Section - Column 2. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
ShowHide Section - Column 3. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
ShowHide Section - Column 4. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
Take control, prevent breaches, and proactively reduce risk
Boost your workload security—and empower your security teams—with our AI-powered Trend Vision One™ – Attack Surface Risk Management for Cloud (ASRM for Cloud) solution.
Proactively reduce your cyber risk with continuous discovery, real-time assessments, and automated mitigation across your cloud environments.
Learn more→
Section 1 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 1 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Level up your workload security with these ASRM for Cloud capabilities:
Continuous asset discovery
Enable continuous attack surface discovery across workloads, containers, application programming interfaces (APIs), and cloud assets.
Actionable risk insights
Harness contextualized risk assessments, analyses, and scoring capable of recognizing high-risk cloud assets.
Automated risk mitigation
Initiate automated security playbooks to orchestrate response across multiple vectors and dramatically reduce your risk exposure.
New: Cloud infrastructure entitlement management (CIEM)
Discover an essential tool for securing your cloud infrastructure, helping you effectively manage and right-size your entitlements.

Section 2 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 2 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
- How-to video: Update from Trend Cloud One™ to Trend Vision One™
- How-to video: Connect your cloud accounts in ASRM for Cloud
- Knowledge Base: Step-by-step guide for onboarding
- Learn more about attack surface risk management (ASRM)
- Learn more about cloud security
- Infographic: Cloud attack surface management
Section 3 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 3 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Simplify your decision
Section 4 - Column 1. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 4 - Column 2. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 4 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 4 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Simplify your decision
Section 5 - Column 1. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 5 - Column 2. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 5 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 5 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.

