Slash your cyber risk with
attack surface management
and cloud resilience
Book a meeting→
Learn how to update →

Agenda Table Headline
| Agenda Day | Session | Speaker |
|---|---|---|
| 8:00 - 8:30 | Reception Coffee | |
| 8:30 - 9:00 | Welcome & Opening Words | Mark Hamill - Manager Cyber Threat Intelligence |
| 09:30 - 10:00 | Keynote 1 | Carrie Fisher - Director Product Manager & Operations |
| 10:00 - 10:30 | Lunch Break | |
| 10:30 - 11:00 | KeyNote 2 | Anthony Daniels - Product Manager |
| 11:00 - 11:15 | Coffe Break |
Overlapping Image Section Headline

Lorem Ipsum is simply dummy text of the.
Lorem ibsumLorem Ipsum is simply dummy text of the printing and typesetting industry?
Lorem ibsumSimplify your decision
ShowHide Section - Column 1. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
ShowHide Section - Column 2. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
ShowHide Section - Column 3. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
ShowHide Section - Column 4. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
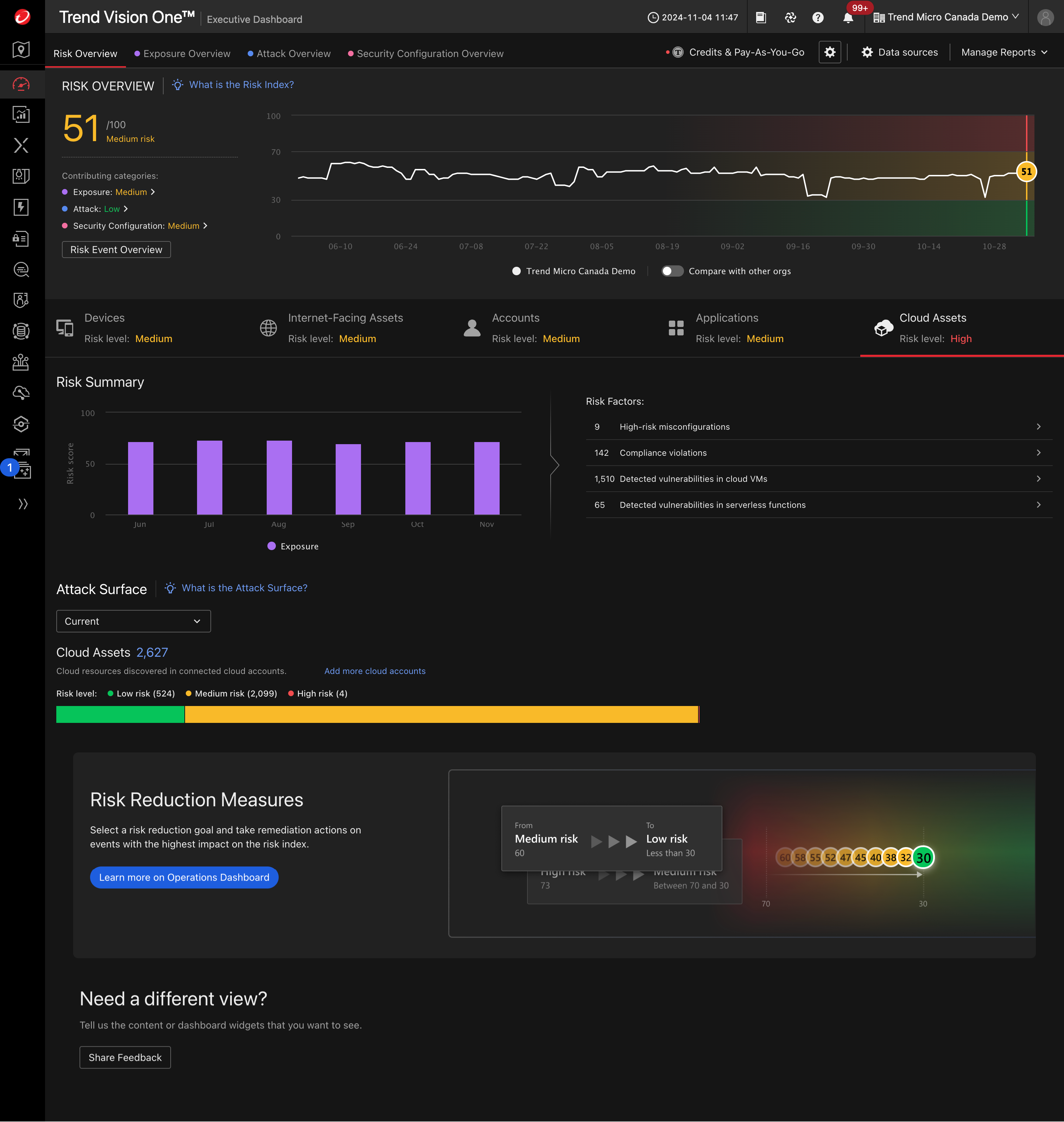
Take control, prevent breaches, and proactively reduce risk
Boost your workload security—and empower your security teams—with our AI-powered Trend Vision One™ – Attack Surface Risk Management for Cloud (ASRM for Cloud) solution.
Proactively reduce your cyber risk with continuous discovery, real-time assessments, and automated mitigation across your cloud environments.
Learn more→
Section 1 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 1 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Level up your workload security with these ASRM for Cloud capabilities:
Continuous asset discovery
Enable continuous attack surface discovery across workloads, containers, application programming interfaces (APIs), and cloud assets.
Actionable risk insights
Harness contextualized risk assessments, analyses, and scoring capable of recognizing high-risk cloud assets.
Automated risk mitigation
Initiate automated security playbooks to orchestrate response across multiple vectors and dramatically reduce your risk exposure.
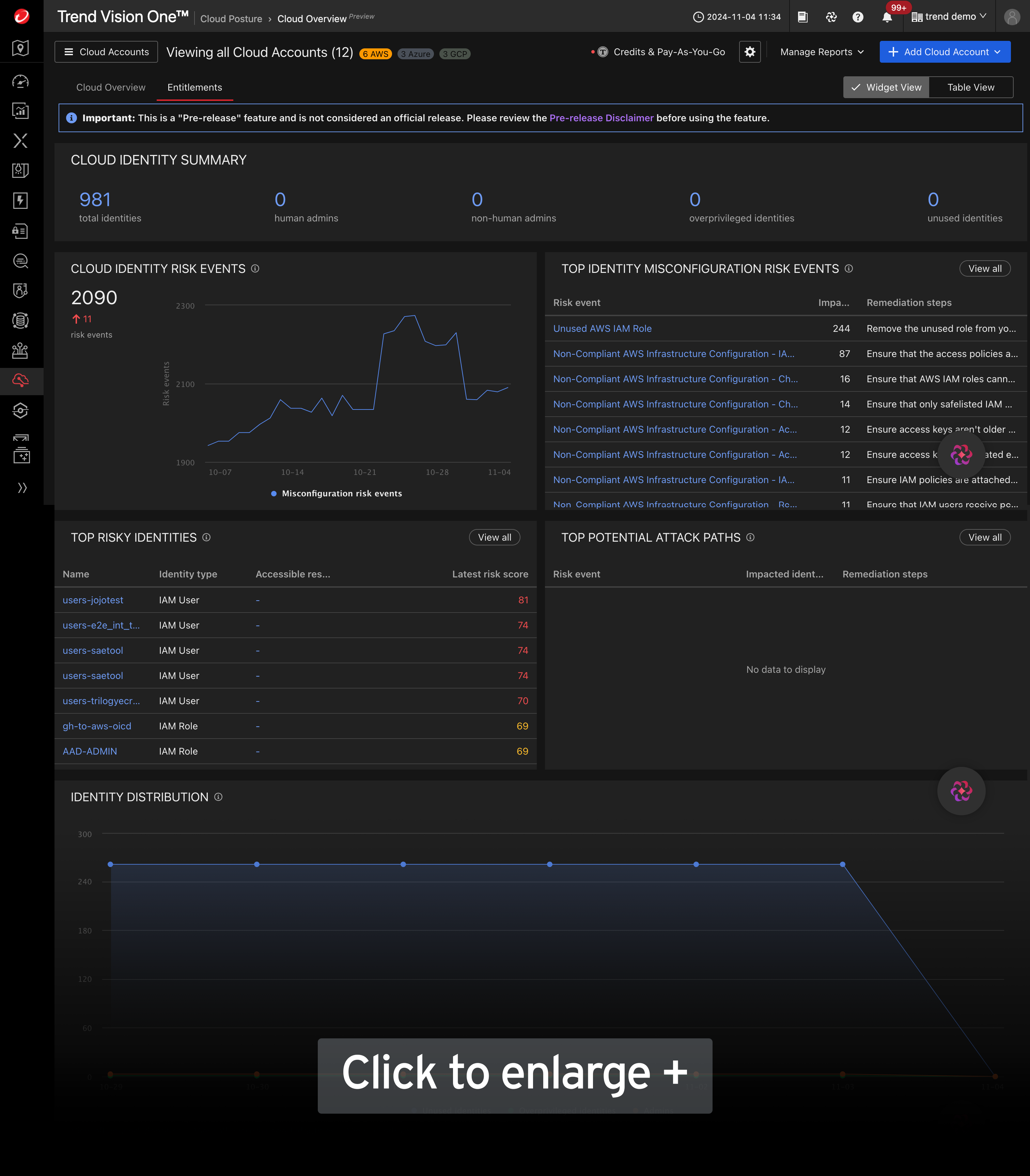
New: Cloud infrastructure entitlement management (CIEM)
Discover an essential tool for securing your cloud infrastructure, helping you effectively manage and right-size your entitlements.
Section 2 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 2 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
- How-to video: Update from Trend Cloud One™ to Trend Vision One™
- How-to video: Connect your cloud accounts in ASRM for Cloud
- Knowledge Base: Step-by-step guide for onboarding
- Learn more about attack surface risk management (ASRM)
- Learn more about cloud security
- Infographic: Cloud attack surface management
Section 3 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 3 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Simplify your decision
Section 4 - Column 1. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 4 - Column 2. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 4 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 4 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Simplify your decision
Section 5 - Column 1. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 5 - Column 2. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 5 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 5 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.