Trend Micro Managed Detection and Response (MDR)
通過
MITRE Engenuity ATT&CK™
Evaluations的嚴苛考驗
閱讀報告→
How can we help?
|
Technical query |
|
|
General inquiry |
Trend guards your privacy. Read our privacy policy.
Thank you. We will contact you soon.
Trend Service One™
Augment threat detection with expertly managed detection and response (MDR) for email, endpoints, servers, cloud workloads, and networks. 24/7 service reduces the burden and time to identify, investigate, and respond to threats.
Learn more →

趨勢科技展現100%
的威脅偵測率
MITRE Engenuity ATT&CK Evaluations 評測採用menuPass 和 BlackCat/AlphV 駭客集團的攻擊手法來考驗 Trend Vision One 託管式服務。
我們很驕傲能延續自 2020 年立下的領先傳統,在所有 15 個主要攻擊步驟當中都展現100% 的偵測率
Trend MDR 憑藉著豐富的內建原生功能與領先的威脅情報,讓網路攻擊無法實現。請閱讀這份報告來進一步了解詳情。
NO AGENT MIGRATION
A simple update that you can complete on your own, all at once or in stages. Your policies, roles, exclusions, and permissions are preserved.
NO LICENSE CHANGE REQUIRED
Update whenever you’re ready, your existing Trend Micro Apex One or Trend Cloud One Endpoint/Workload Security product license will be used in Endpoint Security for licensing. No need to contact Trend to change the product name on your license – we can take care of that at your next renewal call.
ShowHide Section - Column 3. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
ShowHide Section - Column 4. Praesent
non velit ut libero condimentum
pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere
rutrum sodales. Nam id elit ac sem
iaculis lacinia posuere vitae metus.
通過考驗的資安防護
全世界企業都仰賴趨勢科技 MDR 服務來偵測駭客的攻擊,並隨時掌握,不論攻擊如何散播或從哪裡開始擴散。
Trend Vision One 託管式服務內含主動式威脅追蹤以便更快發掘威脅,並提供 7 天 24 小時監控,在事件發生當下立即回應,同時還透過各種最佳化調校來降低您的資安風險。
請閱讀 MITRE Engenuity ATT&CK Evaluations 的完整報告來了解趨勢科技 MDR 服務如何讓企業的防禦變強。請至此處下載。
Read the complete MITRE Engenuity ATT&CK evaluation report to understand how your defensive posture is stronger with our MDR service. Get it here.
Trend Vision One managed services includes proactive threat hunting to identify threats sooner, 24/7 expert response to incidents when they occur, and a wide range of optimizations to reduce cyber risk.
Read the complete MITRE Engenuity ATT&CK evaluation report to understand how your defensive posture is stronger with our MDR service. Get it here.
Section 2 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Vulnerabilities, both known and unknown, present an opportunity for threat actors to exploit and gain access to your network and beyond. With critical and high-severity application and operating system threats increasing every year, it’s important for you to understand, communicate, and mitigate the cyber risk that arises from vulnerabilities—even the ones you don’t see coming.
GRAPHIC?

Advanced threat correlation:
- Connect deep activity data across multiple security vectors and third-party integrations
- Identify and connect suspicious events.
- Native sensors, combined with third-party data inputs, feed analytics and detection models
Section 3 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Continuous asset discovery
Gain visibility of assets across security layers in data center, cloud, and hybrid environments.
Actionable risk insights
Utilize contextualized risk assessment, analysis, and scoring capable of recognizing which assets pose the highest risk.
Automated risk mitigation
Initiate automated security playbooks to orchestrate response across multiple vectors.
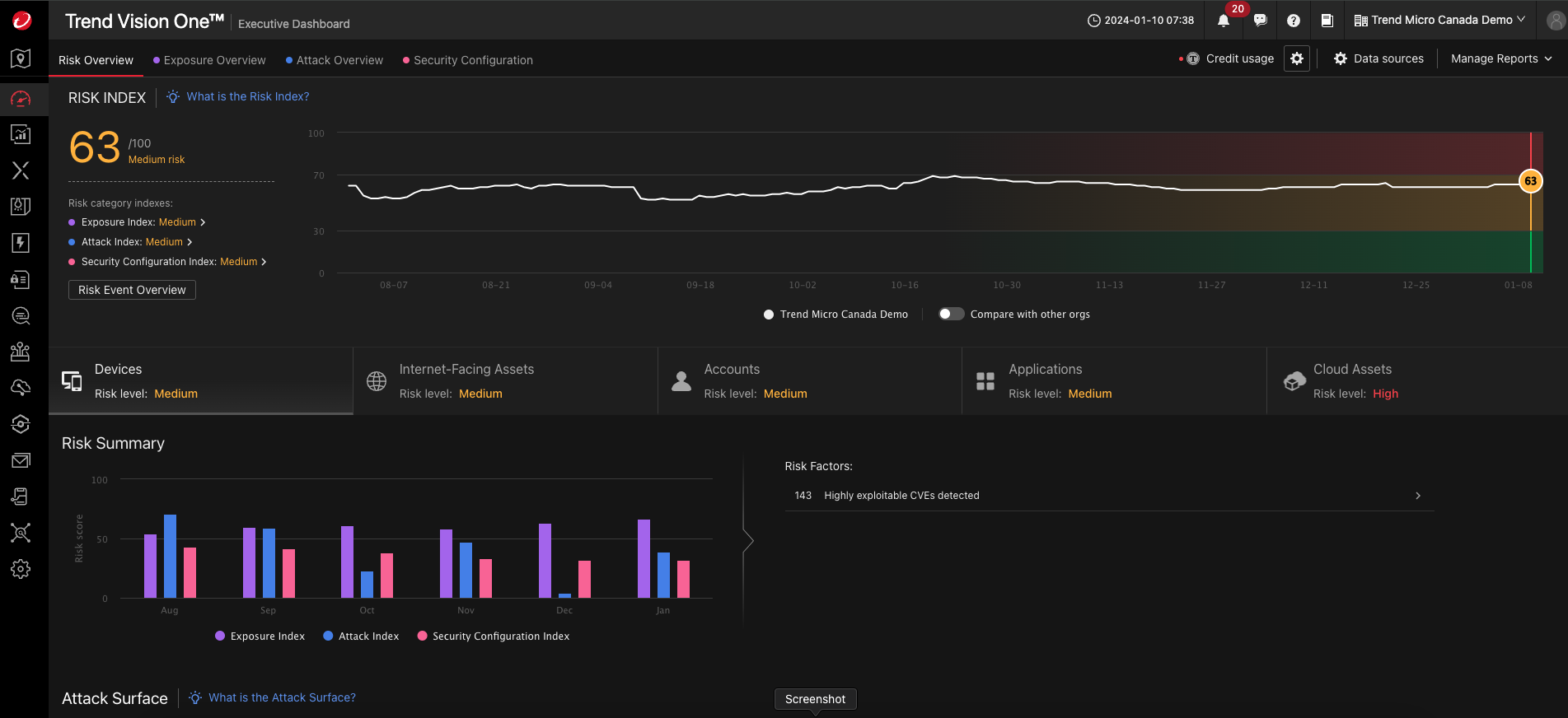

Automated risk mitigation
- Leverage AI and machine learning to synthesize vulnerabilities, risks, security controls, and overall posture for custom remediation recommendations
- Effortlessly deploy risk remediation suggestions across the attack surface
- Initiate automated security playbooks to orchestrate response across multiple vectors
Section 4 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Trend Vision One essentials
Endpoint security demo
ASRM + XDR solution brief
How to connect guide
How to connect demo
Supported features for Trend Vision One
Trend Vision One Essentials
Endpoint Security Demo
ASRM + XDR solution brief
Trend Vision One 30-day trial
Endpoint Security Management FAQ
Endpoint Security Datasheet
Cybersecurity Consolidation e-book
Configuring Deep Security Software
Getting Started with Endpoint Security
How to deploy agents with SCCM
Supported features and discrepancies
Data Collection Notice
Section 5 - Column 3. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
Section 5 - Column 4. Praesent non velit ut libero
condimentum pulvinar sed vitae tellus.
Vestibulum
id tristique elit. Suspendisse posuere rutrum
sodales. Nam id elit ac sem iaculis lacinia
posuere vitae metus.
