Trend Micro Cloud One™ Webinar Series:
SECURING YOUR JOURNEY TO THE CLOUD
Unlimited opportunities and new business models are the two most important reasons why companies are moving to the cloud. But these factors might cause new challenges arise, especially in the area of IT security.
With Cloud One, Trend Micro presents our version of the most innovative security platform that not only solves customers' technical problems, but also demonstrates and enables conceptual flexibility and agility.
As we want to present the new solution platform in details and explain its advantages, we have prepared a series of webinars for you to see the various options of its use. Sign up, watch our webinars and see Cloud One in action!
Section 1 - Column 2. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 1 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 1 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Webinar#1: Meet Cloud One - cloud security redefined
15.09.2020, @10:00 CEST
The first webinar of this series is about the Cloud One concept - a new security platform dedicated to protect cloud and hybrid environments. Topics will cover:
- Challenges related to protection of cloud and hybrid environments
- Workload Security in cloud and hybrid environments
- Secure development of services and applications according to DevSecOps methodology
- Compliance assurance and risk management in cloud environments
Section 2 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 2 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
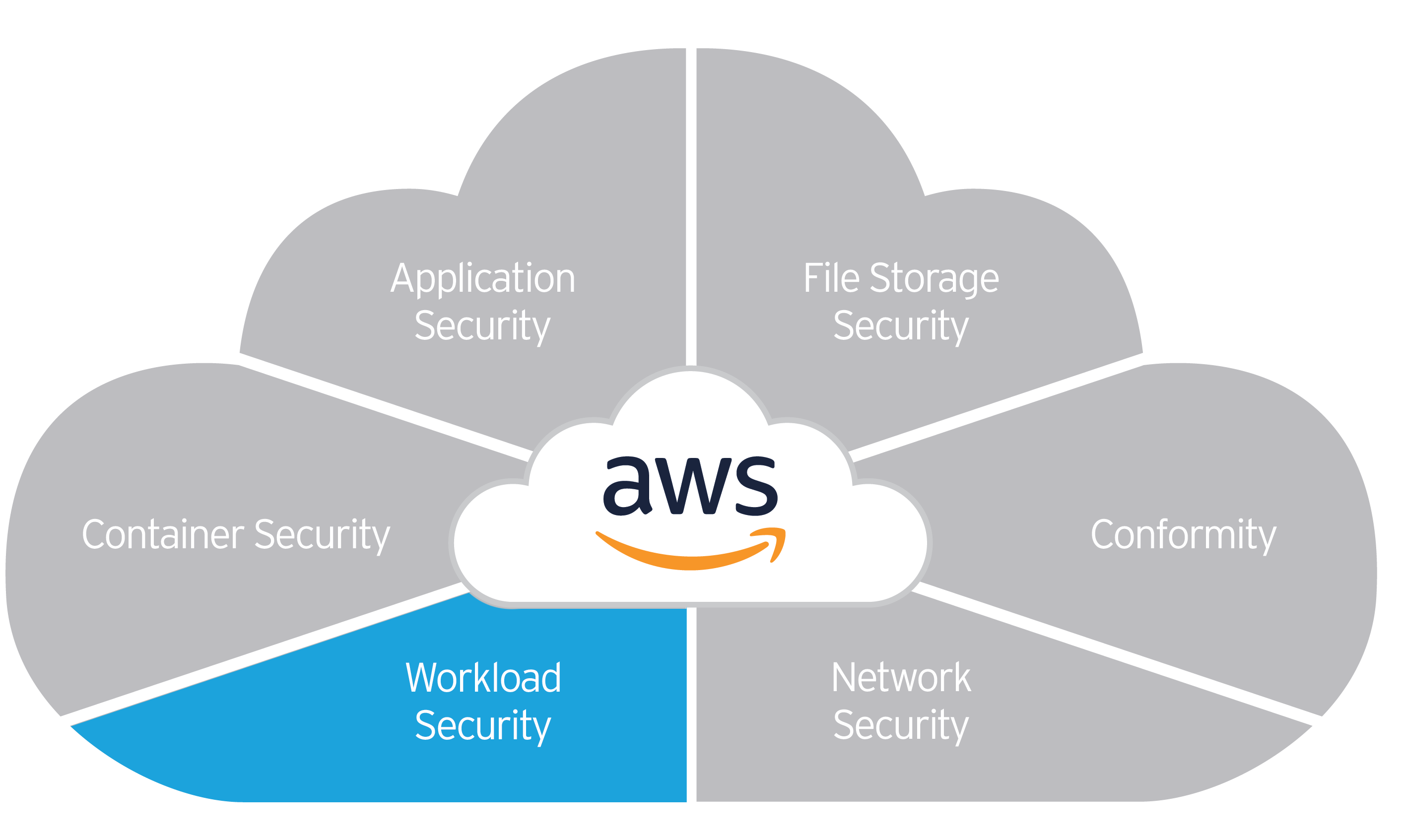
Webinar #2: Cloud One Workload Security
22.09.2020, @10:00 CEST
Trend Micro Cloud One™ - Workload Security provides comprehensive server protection regardless of the operating system version and the runtime environment. It protects against attacks that exploit the operating system, services and applications vulnerabilities using virtual patches. During the second webinar in the Securing Your Journey to the Cloud series, we will discuss the following topics:
- Security mechanisms and supported platforms
- The basics of automation and integration
- Typical use case scenarios: Data Center, Cloud Migration, DevOps.
Section 3 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 3 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
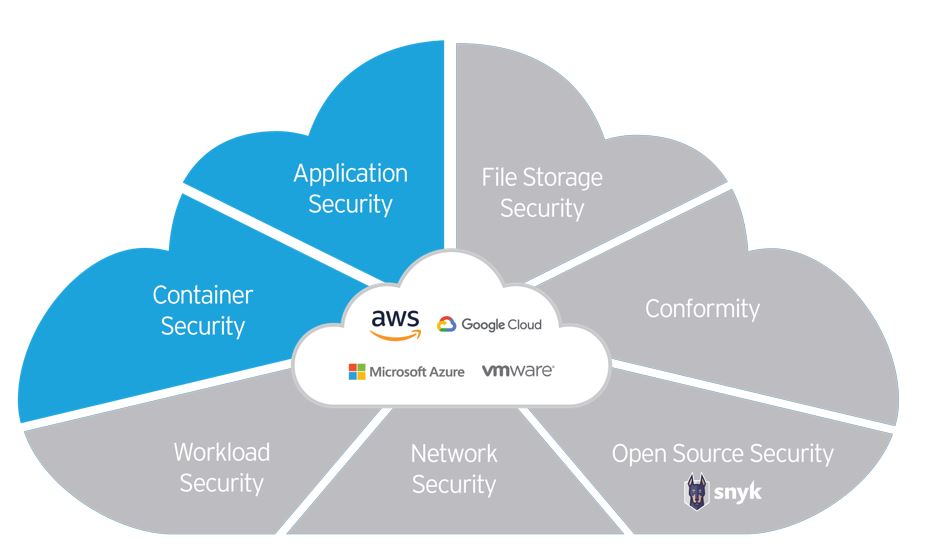
Webinar#3: DevOps Security - the best-in-class protection for DevOps and cloud-native apps
29.09.2020, @10:00 CEST
During the third webinar of the series, we will show you how you can:
- Early detect the cyber-security problems in DevOps environment
- Discover vulnerabilities, malware and confidential data in the container image before it is launched
- Quickly and seamlessly implement security in the application code
Section 4 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 4 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
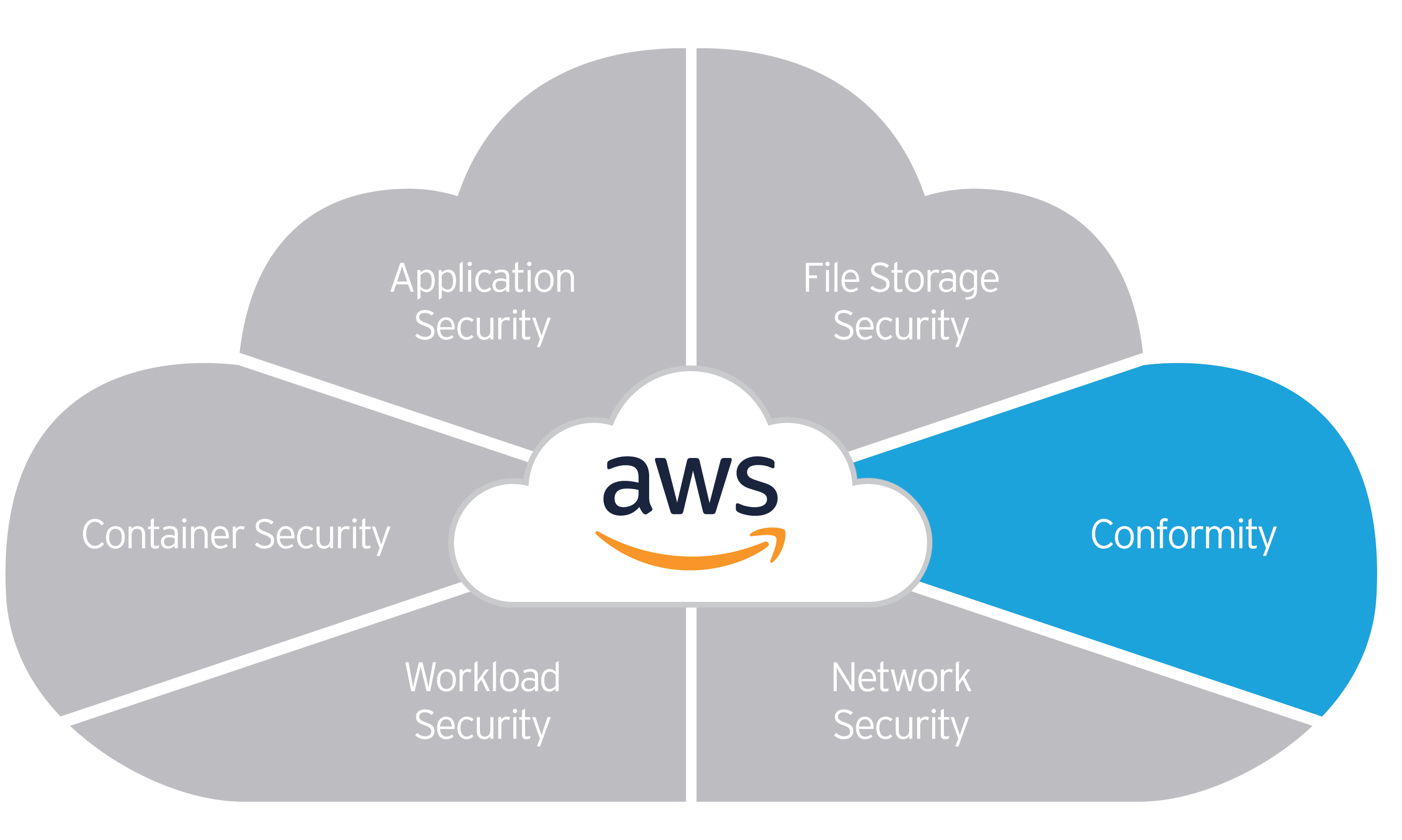
Webinar#4: Cloud One Conformity - security and data protection across multi-cloud environments
6.10.2020, @10:00 CEST
Companies are increasingly turning to hybrid architecture, combining classic data centres with private and public clouds. While this allows to work flexiblyg, it also creates new security risks. Here's the invitation to the fourth webinar, where we will address the following topic areas:
- Compliance, including alignment to existing regulations
- Best practices for cloud operations
- AWS Well Architected Framework
- Automatic Security & Compliance Posture Remediation
Section 5 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 5 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
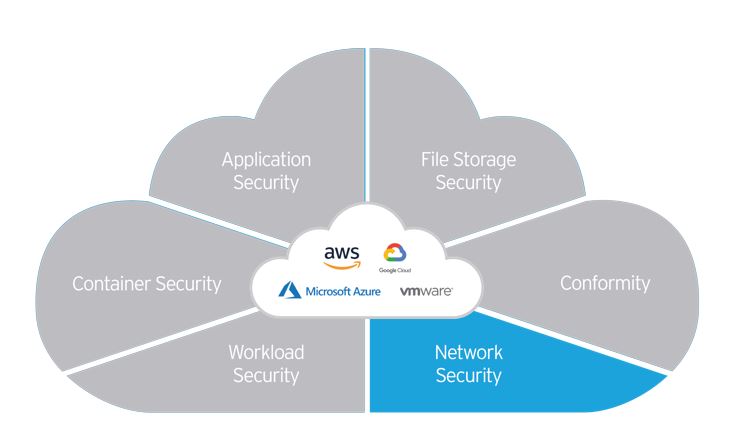
Webinar#5: Cloud One Network Security – How to implement TippingPoint IPS (Intrusion Prevention System) technology in the public cloud
13.10.2020, @10:00 CEST
Nowadays more and more organizations are starting their journey into the public cloud and launch their IT services in a hybrid environment, so there is a growing need to standardize security mechanisms at the network level. Take part in the fifth webinar of the Securing Your Journey to the Cloud series and learn:
- How the reliable IPS (Intrusion Prevention System) technology - Trend Micro TippingPoint - can be deployed in the public cloud and controlled via a single, shared management system
- How you can protect your organization from new, yet undisclosed threats
- How to implement the concept of vulnerability protection through Virtual Patching
Section 6 - Column 3. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.
Section 6 - Column 4. Praesent non velit ut libero condimentum pulvinar sed vitae tellus.
Vestibulum id tristique elit. Suspendisse posuere rutrum sodales. Nam id elit ac sem iaculis lacinia posuere vitae metus.